- Login to your gmail and got to settings.
- Under 'Forwarding and POP/IMAP', enable both POP3 and IMAP.
- Now open your Outlook.
- Add new account and put all the required information.
- Put your incoming mail server as pop.gmail.com
- Put your outgoing mail server as smtp.gmail.com
- Click on the 'More Settings' as you need to enable few things.
- At the 'Outgoing Server' tab, tick on "My outgoing server" and "use the same settings as my incoming mail server"
- Then go to 'Advance' tab, Put the incoming server port as 995 and outgoing server as 465 with SSL connection.
- Save and try your connection. It should works! :)
Sunday, December 14, 2014
Tuesday, November 18, 2014
UTPHax'14 - Writeup for Audio Stego Round 5
Its a great experience handling another hacking contest in a local university recently. As usual, there will be some questions that the contestants were not able to answer it and they keep on asking how the hell are it can be solved?
Well, here's one of the way for this challenge :)
Question : Chill out the pressure and listen to the rhyme. Enjoy!
Participant provided with a WAV where when they play it will hear a nice piano rhythm. However, it seems there's something buggy at the middle of the play.
Hint given
By looking at the hint, we can know that this sound generated from an online tool which can be manipulated using our keyboard.
Simple google for "piano generator" will lead us to this website http://www.gootar.com/piano/ and yes, this is the right URL :)
By default, there's already a piano tone available on the URL and if we play it, woh! it is the similar sound with our question WAV audio.right?!
Open up our audacity and record the sound. Open the original WAV and compare it with our question WAV. It will looks like below.
From the analysis, we can say that the starting and ending point is just like what I squared out in the picture above. So let us see what is actually the key that was used before our flag located is.
Yerp. you are right. ; symbol. So what we should do next? Looking back at our keyboard based piano, we can know that each tone have different frequency (high,high peak,low,etc) as described in the picture below, I divided it into 4 different layer of frequency.
If we hear the sound where our flag located is, the first tone actually belong to the 2nd layer. So back again to the URL, and 1 by 1 we test to capture the sound.
Start the tone with ; then continue with the character in the 2nd layer. As example,
;]_;[_;p_;o -continue yourself- do note that _ symbol actually just a rest tone. so we can hear the tone much clearer.
Once done for that, again record and compare it using audacity. It will look like below.
Aha! we can see some similarities between the sound we created just now with the original question WAV (from the starting point of the flag).
So the flag either start with ;p or ;o
Let us pick p and proceed with a new tone. Hear it back again, and we can say the tone quite low and belong to 3rd layer.
Go to URL, and start recording the tone.
;p;_;pl_;pj_;ph_;pg -blalala continue yourself-
Compare it again with our question WAV.
Auw yeahh!! we are on the right track! Then? just continue the same step until you finish the line. once done you'll get the flag :)
flag is pl4yme
That's all. Thanks!
Well, here's one of the way for this challenge :)
Question : Chill out the pressure and listen to the rhyme. Enjoy!
Participant provided with a WAV where when they play it will hear a nice piano rhythm. However, it seems there's something buggy at the middle of the play.
Hint given
By looking at the hint, we can know that this sound generated from an online tool which can be manipulated using our keyboard.
Simple google for "piano generator" will lead us to this website http://www.gootar.com/piano/ and yes, this is the right URL :)
By default, there's already a piano tone available on the URL and if we play it, woh! it is the similar sound with our question WAV audio.right?!
Open up our audacity and record the sound. Open the original WAV and compare it with our question WAV. It will looks like below.
From the analysis, we can say that the starting and ending point is just like what I squared out in the picture above. So let us see what is actually the key that was used before our flag located is.
Yerp. you are right. ; symbol. So what we should do next? Looking back at our keyboard based piano, we can know that each tone have different frequency (high,high peak,low,etc) as described in the picture below, I divided it into 4 different layer of frequency.
Start the tone with ; then continue with the character in the 2nd layer. As example,
;]_;[_;p_;o -continue yourself- do note that _ symbol actually just a rest tone. so we can hear the tone much clearer.
Once done for that, again record and compare it using audacity. It will look like below.
Aha! we can see some similarities between the sound we created just now with the original question WAV (from the starting point of the flag).
So the flag either start with ;p or ;o
Let us pick p and proceed with a new tone. Hear it back again, and we can say the tone quite low and belong to 3rd layer.
Go to URL, and start recording the tone.
;p;_;pl_;pj_;ph_;pg -blalala continue yourself-
Compare it again with our question WAV.
Auw yeahh!! we are on the right track! Then? just continue the same step until you finish the line. once done you'll get the flag :)
flag is pl4yme
That's all. Thanks!
Sunday, August 3, 2014
I hate you, so I pawn your Google Open Gallery
Hi, long time no see. Quite busy with works and probably will not able to update too much in future.
Going to share with you guys another bug I found in Google.
The bug as shown below.
Google is currently open service port 80 and 443. These ports are exposing what kind of service they're using. This bug worth $10k. Ok. Just a joke. Lets be serious.
Last time I found a bug in one of Google's service, Open Gallery. Using this service, it allows a user to share their exhibition art stuff (sorta) and each of the exhibition will be given a specific URL at *.culturalspot.org domain. And, this domain cannot be changed once we saved the name.
I created two different account for Open Gallery.
I have some revenge at prakhar's_motorbike@gmail.com, and luckily this guy currently selling his arts using Open Gallery (test333.culturalspot.org). Lets pawn his Open Gallery!
What I'm doing below shows that
That's all guys. Have fun.
This was fixed by Google Team :)
Going to share with you guys another bug I found in Google.
The bug as shown below.
Google is currently open service port 80 and 443. These ports are exposing what kind of service they're using. This bug worth $10k. Ok. Just a joke. Lets be serious.
Last time I found a bug in one of Google's service, Open Gallery. Using this service, it allows a user to share their exhibition art stuff (sorta) and each of the exhibition will be given a specific URL at *.culturalspot.org domain. And, this domain cannot be changed once we saved the name.
I created two different account for Open Gallery.
- jablor.culturalspot.org (using attacker@gmail.com) -
- test333.culturalspot.org (using prakhar's_motorbike@gmail.com)
 |
| jablor.culturalspot.org |
 | |||||||||
| test333.culturalspot.org |
What I'm doing below shows that
- I run up my Burpsuite in my account and try to save my current setting.
- I trapped the request during the saving process and change my domain from jablor.culturalspot.org into my target's URL, test333.culturalspot.org
- What happen? His Open Gallery stuff changed into mine and his domain owned by me. He will see his domain as my content and the content itself will be controlled by me. :)
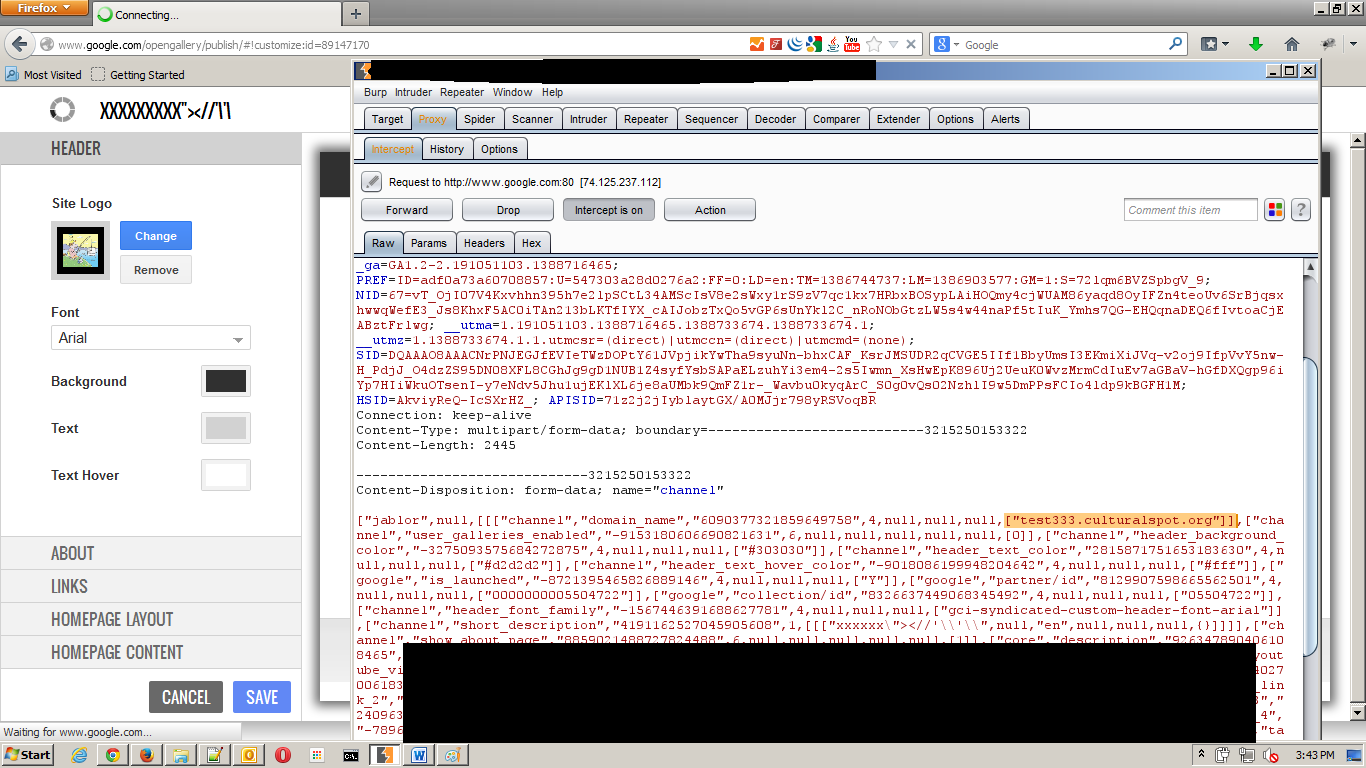 |
| Trigger up Burp and change the domain |
 |
| My original culturalspot will be non-exist as its already changed into victim's URL |
 |
| Victim's culturalspot with my content :) |
That's all guys. Have fun.
This was fixed by Google Team :)
Wednesday, June 11, 2014
XSS in Google MapMaker
Hi,
Its been a while..just get back to my blog and what I can see is similar to..
sorry my dearie blog.
Ok. Going to share my old bug with Google BugBounty VRP. Its an XSS in the MapMaker,a tool to create/modify the Google Map I assume.
The bug exist on the comment form.
1 - Find any place(s) that you want to edit.
2 - Go to comment form and put your XSS payload. Easy Pitsy! :D
cio :)
Its been a while..just get back to my blog and what I can see is similar to..
sorry my dearie blog.
Ok. Going to share my old bug with Google BugBounty VRP. Its an XSS in the MapMaker,a tool to create/modify the Google Map I assume.
The bug exist on the comment form.
1 - Find any place(s) that you want to edit.
2 - Go to comment form and put your XSS payload. Easy Pitsy! :D
oh yea..your "><img src=x> and <a href=x> payload wont working for this case. Seems there's some filter happening in case we are using those payloads. Luckily, they missed-out <iframe> :)
Sunday, February 2, 2014
Youtube - Stored XSS Strikes Back!
Hi,
Simple right?
Till next time,adios!
@yappare
10 January 2013 : Reported to Google
11 January 2013 : Received notification from Aleksandr, Google Security Team
12-14 January 2013 : Bug noticed was fixed around this date.
15 January 2013 : Received email regarding reward
22 January 2013 : Confirmation of fix from Google's team.
#edit: Prakhar my friend said that this XSS actually execute on youtube main domain as well since he was double check for me on that day and it work in www.youtube.com. sadly I dont have the screenshot as a proof
Remember above picture? Most of you might thought its an XSS vulnerability in Gmail, sad to say it is not.haha..The bug actually exist in Youtube Api. Yes, similar to my previous post Yay the Nay in Youtube, this bug also came from the same Youtube Api.
The vulnerable parameter was track's name. Interesting part is, if you try to use XSS payload directly as track's name, it won't working. An error will appear saying you're trying to use special characters that are not allowed.
But due a glitch occur in this section, I was able to change the track's name by using "edit" function. By directly replay the request or tamper it, I can change the old_name into a new name with my XSS payload as shown below.
Once saved, the XSS successfully stored in my video. So does it mean if you watch the video from www.youtube.com it'll executed? Sadly, no. However, the XSS can be executed in Gmail, Google Docs/Presentation and Google Plus. This is because the video will be played using Google's player that was affected with this vulnerability.
Till next time,adios!
@yappare
10 January 2013 : Reported to Google
11 January 2013 : Received notification from Aleksandr, Google Security Team
12-14 January 2013 : Bug noticed was fixed around this date.
15 January 2013 : Received email regarding reward
22 January 2013 : Confirmation of fix from Google's team.
#edit: Prakhar my friend said that this XSS actually execute on youtube main domain as well since he was double check for me on that day and it work in www.youtube.com. sadly I dont have the screenshot as a proof
Tuesday, January 14, 2014
Again, from Nay to Yay in Google Vulnerability Reward Program!
Happy new year to everyone. This is my first post for 2014.
On 9th January 2014, I posted this on my twitter
So is this post related to that? Will get to it soon or probably next month.haha..
On 9th January 2014, I posted this on my twitter
 |
| https://twitter.com/yappare/status/421470672330571777/photo/1 |
In this post I'm going to share to you a bug that manage me to be inside Google Vulnerability Reward Program G+ Community here
The bug is a Self Stored XSS in Youtube. Yerp..
Let us see how the XSS exist.
- In Youtube video manager, there's a function for a user to create Captions for his/her video(s).
- Put our XSS payload in the script box and save.
- Once we play the video, our XSS will be executed.
- Check on below screenshots :)
But..there's a problem! The XSS only executing in Caption's Video Manager. Which in other word the XSS is only stored for that user only.
Hmmm...
There's must be a way to exploit or to manipulate this vulnerability. Last time I managed to find a way to Yaying this Nay in Google Adwords. You guys can check on it http://c0rni3sm.blogspot.com/2013/12/google-adwords-stored-xss-from-nay-to.html
I browsed a few times to see is there any share or embed function in this Captions thing. And then..
I noticed that, there's a function where a user can request for a translation from 3rd party or other users. So how this function working?
- User request for his/her video for a translation.
- User able to choose either from 3rd party or by other Google Users.
Manipulating time.Let assume that, there's a community for English series, Movies, Korean dramas that have some translator for Youtube's caption..and among them, there's an attacker >: )
- Attacker will received the invitation.
- Attacker put his/her evil code in the middle of translations.
- Send to the requester for approval.
Once done, the requester will get an email notification and what she/he need to do is review the translated caption and approve it. So what happen next? The XSS will be executed
and
Till next time, adios!
@yappare
03 December 2013 - Reported via VRP form
07 December 2013 - Received a reply from Martin,Google Security Team
07 December 2013 - Google Team asked for more information to reproduce
08-10 December 2013 - Fixed around these dates.
11 December 2013 - Received a reward email from Google
10 January 2014 - Kevin,Google Security Team confirmed the fix.

























