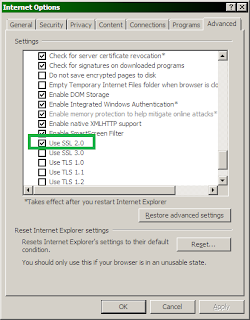
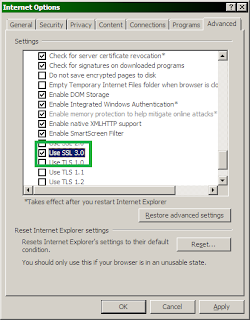
1 - copy your wallpaper to the
/usr/share/backgrounds/laughlin/default/wide/
/usr/share/backgrounds/laughlin/default/standard/
/usr/share/backgrounds/laughlin/default/normalish/
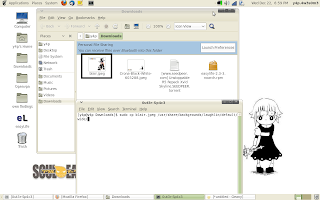
make sure you do it with root privilige.
2 - go to the /usr/share/backgrounds/laughlin/default/ directory
3 - edit the laughlin.xml using vi
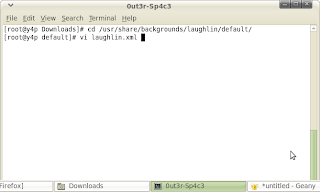
4 - change the wallpaper to your wallpaper that just copied before.
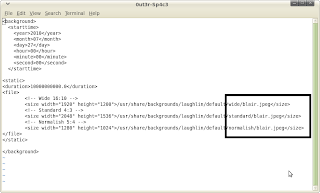
5 - Save, and complete!
You can see your login page with a new wallpaper.
kudos to http://aenguillo.wordpress.com
/usr/share/backgrounds/laughlin/default/wide/
/usr/share/backgrounds/laughlin/default/standard/
/usr/share/backgrounds/laughlin/default/normalish/

make sure you do it with root privilige.
2 - go to the /usr/share/backgrounds/laughlin/default/ directory
3 - edit the laughlin.xml using vi

4 - change the wallpaper to your wallpaper that just copied before.

5 - Save, and complete!
You can see your login page with a new wallpaper.
kudos to http://aenguillo.wordpress.com